- Web hosting
- Services
- Help
Knowledge base
How to connect to a server with SSH?
SSH protocol is intended for securing the connection between the user and remote server.
What is SSH protocol?
SSH (for Secure Shell) is an application-level network encryption protocol that provides secure remote connection to operating system when using insecure network such as the Internet.
In order to safely transmit data on the Internet from the client to the server, a secure channel is required, guaranteeing the integrity, validity and privacy of the transmitted information. SSH protocol communication channel provides precisely this type of connection.
SSH server is installed on a remote machine, while a SSH client is used on the computer a connection to the server originates from.
Using a secure channel of communication via SSH, you can freely transfer any data, use the command line, run applications on the server, etc.; all operations will be securely encrypted. SSH protocol compresses all the outgoing data, encrypts it, and then transfers it to the server or vice versa.
Through SSH you can run Unix-based operating systems graphical interface, similar to how you may know it in Windows OS. This is done using X11 Forwarding mechanism.
What makes SSH secure?
The data transmitted via SSH channel is encrypted with special algorithms, and then transferred. If an intruder succeeds in intercepting some information during transmission from the client to the server, he will not be able to decipher it.
Before connecting, SSH client authenticates the server (checks its authenticity), then the SSH server authenticates the client. There are several authentication algorithms (passwords, keys, etc.), and they are all equally reliable.
Another factor that adds to security of a SSH connection is the algorithms’ effect on the prevention of hacker attacks.
Due to these factors, SSH is protected from the major kinds of hacking activities, such as IP- and DNS spoofing, when IP-address or an entry in DNS are replaced, and data is transmitted to the spoofed address or domain name is transmitted to the intruder. In addition, the use of SSH provides protection against open data interception through the Internet.
SSH protocol versions
There are both free and paid (commercial) versions of the SSH protocol.
OpenSSH is a free protocol preset on all operating systems of the Unix kernel; it exists in the form of a utility consisting of SSH client and SSH server.
SSH Communications Security is the commercial version of the protocol. It is slightly different from OpenSSH, while its basic functionality is identical to that of the free version. It provides tools for managing via the web, commercial servicing, and some other functions.
Currently there are two SSH protocol versions that were released in chronological order (SSH-1 and SSH-2). The second version is more advanced; it prevents MITM type attacks.
SFTP protocol
SFTP (for SSH File Transfer Protocol) is a network protocol, an extension to SSH-2 protocol for secure transfer to a remote server over an insecure network. Just like SSH protocol, it runs on the network layer and consists of two parts: SFTP server and SFTP client.
SFTP is designed so that it does not perform authentication and provide secure connection itself, but is installed “on top” of the secure channel. For example, first the connection is made to a remote server via SSH, next file transfer via SFTP begins. Other cryptographic protocols that provide reliable connection may be used with SFTP.
FTP and SCP protocols are SFTP predecessors; they are in fact its out-dated versions. They may not provide such features as file transfer interruption and resumption, date/time stamp for each file, etc.
OpenSSH includes SFTP server and SFTP client.
SSH and SFTP protocols application
SSH protocol is used for secure remote server administration, while SFTP – for file transfer and management via SSH connection.
For example, you rented a virtual or dedicated server and you need to transfer your data (website, email, images, etc.). To prevent data interception or damage during the transfer process, as well as to speed up file copying, use SSH protocol.
The commands run by SSH client are different for various operating systems. UNIX-like operating systems include a set of commands for working with SSH via the command line; for Windows there are GUI shells (free client shells such as PuTTY, WinSCP, etc.).
Example of connection via SSH
Let us assume your home computer runs on Windows, and the remote server runs on Linux. In this case, we recommend using the free PuTTY shell for establishing SSH connection. Download PuTTY application (it consists of one .exe file and does not require installation).
Launch putty.exe
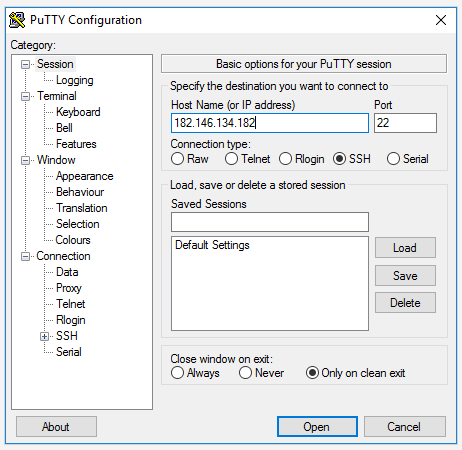
Be sure the port number is 22, and select SSH connection type.
You only need to fill in the Host Name (or IP address), specifying the remote server name and its IP address (preferred). Click Open.
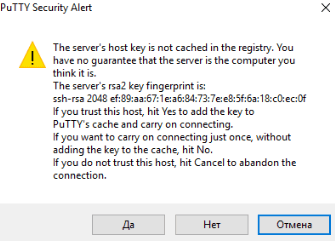
PuTTY Security Alert notifies that there is no guarantee that the server is the computer you think it is, since the server’s key is not cached in your computer’s memory. Hit “Yes” if the IP address you entered is correct.
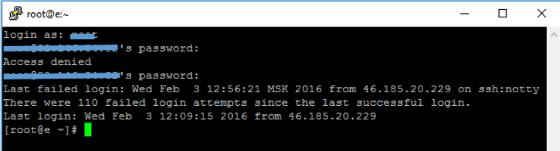
Next, enter the user name and password to access the remote server.
When entering the password, note that the characters you enter will not appear on the command line. You only need to enter your password (with no spaces) and press Enter.
In case of a successful connection, the server command line will appear.